This article is a part of a series on Cryptography. Use the navigation boxes to view the rest of the articles.
Confidentiality is the concept of hiding or scrambling your data so that only the intended recipient has access. This is typically accomplished by some means of Encryption.
Data before it has been encrypted is referred to as Plain text, or Clear text. After the data has been encrypted, it is referred to as Cipher text. The Cipher text should be completely unrecognizable, revealing no patterns or hints as to what the original Plain text was. Only the intended receiver(s) should have the ability to Decrypt the Cipher text and extract the original Plain text.
The process by which the the Plain text is converted to Cipher text is known as the Encryption Algorithm.

In this basic encryption example, all that is needed to reverse the encryption and decrypt the Cipher text is insight into what happened in the Encryption Algorithm. You’ve probably picked up by now, that to take hello and scramble it to lohel, all I did was shift the letters forward twice. To undo this, you just need to shift the letters back twice.
There are, however, a few issues with this type of basic encryption:
- It does not scale. For each new person you wish to securely exchange data with, you would need to devise a new encryption algorithm. You wouldn’t want the communication you had between you and your bank to be secured the same way as it was between you and your employer. How many different algorithms could you come up with before you were forced to reuse them?
- Once the algorithm is discovered, the security is comprised for all time. Everything that was secured with the compromised algorithm in the past is now fully decryptable. And everything that you might ever continue to secure with that algorithm in the future is now fully decryptable.
- In the end, all you’ve done is obfuscate the data. It may be enough to prevent a passerby from accidentally reading your Clear text, but it won’t be enough to thwart a truly determined hacker.
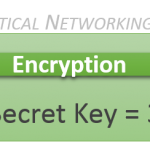
As a result of these weaknesses, modern confidentiality makes use of what is sometimes referred to as Cryptographic Encryption. Which is combining a publicly known encryption algorithm along with a secret key.
The math behind the algorithm is publicly disclosed, which gives it the benefit of having been vetted by many mathematicians and cryptographers before any particular algorithm is accepted for common use.
The secret key can be a randomly generated set of characters — which makes it easy to produce. It is not difficult to use a different key for each entity you wish to speak securely with, even if the algorithm for each of these parties is the exact same. It is also not difficult to periodically regenerate the secret key, so even if a particular key becomes compromised, only a subset of your communication can be decoded.
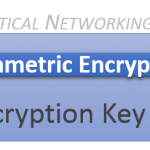
There are two types of Cryptographic Encryption: Symmetric Encryption and Asymmetric Encryption. The main difference between the two types of encryption can be summarized as follows:
- Symmetric encryption – Encrypt and Decrypt using the same key.
- Asymmetric encryption – Encrypt and Decrypt using two different keys.
We will look at both of these and how they are used to provide Confidentiality in more detail in next articles in this series.