This article is a part of a series on Cryptography. Use the navigation boxes to view the rest of the articles.
Earlier, we learned that Symmetric encryption is an encryption scheme that uses the same key to encrypt and decrypt. Conversely, Asymmetric encryption, uses different keys to encrypt and decrypt. Lets take a look at a simple example.
For the sake of simplicity, let us pretend for this example that there are only the lower case letters a - z available. No capitals, no numbers, no symbols. This would give us a total of 26 possible characters.
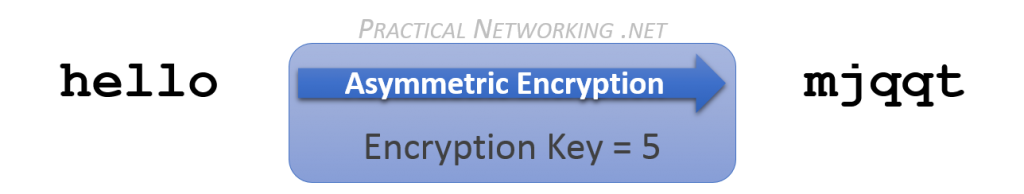
In the example above, we are taking the plain text of hello, and encrypting it with an Asymmetric encryption key of 5. This results in our cipher text, mjqqt.
Instead of simply reversing the encryption, as you would for a Symmetric encryption, let us instead continue rotating the letters forward 21 more times:

Notice if we continue to move forward, with a Decryption key of 21, we end up back where we started at the original plain text of hello.
Now obviously, in this simplistic example, we could have simply rotated backwards with the Encryption key of 5. But in a real Asymmetric encryption algorithm, attempting to re-use the Encryption key (either forwards or backwards) would simply scramble the text further.
That said, there is something significant worth pointing out that we can learn from the Asymmetric encryption example above.
We used an Encryption key of 5, and were able to decrypt successfully with a Decryption key of 21. BUT, we could also have used an Encryption key of 21, and a successfully decrypted with a Decryption key of 5. The Asymmetric keys are mathematically linked. What one key encrypts, only the other can decrypt — and vice versa.
Can you determine another set of keys that would work as an Asymmetric key pair for the simple example above?
A Tale of Two Keys
So what can we do with an Asymmetric Key Pair?
We discussed earlier the existence of the two keys — that they are mathematically linked, and that whatever data is encrypted by one of the keys can only be decrypted by the other key.
![]() One of these keys is stored securely, and never shared with anyone else. This key is from then on referred to as the Private Key. In the rest of this series, this key will always be checkered, and point to the left.
One of these keys is stored securely, and never shared with anyone else. This key is from then on referred to as the Private Key. In the rest of this series, this key will always be checkered, and point to the left.
![]() The other key is made available to the world. This key then becomes your Public Key. In the rest of the series, this key will always be solid colored, and pointing to the right. The “key pair” will be identified by the matching color.
The other key is made available to the world. This key then becomes your Public Key. In the rest of the series, this key will always be solid colored, and pointing to the right. The “key pair” will be identified by the matching color.
Every participant in Asymmetric encryption has their own, unique key pair. Each of these keys can be used in different ways in order to attain different security features. These will be outlined in a dedicated article in this series.
Comparison with Symmetric Encryption
Understandably, the math involved in Asymmetric encryption is slightly more complex than what might be required with Symmetric encryption. As a result, the CPU cost of Asymmetric encryption tends to be higher than its symmetric counterpart.
Moreover, a side effect of the math is also that the resulting cipher text often ends up being larger than the original plain text. If you only intend to Asymmetrically encrypt a small amount of text, then this is negligible. But if you are looking to encrypt bulk data transfer, this makes Asymmetric encryption not ideal.
That said, the primary (and most significant) benefit to using Asymmetric encryption is the Private Key never needs to be shared. As opposed to Symmetric encryption, where the same Secret Key must exist on both sides of the conversation.
As a result, Asymmetric encryption is regarded as more secure than its symmetric counterpart. There is no risk of compromise while the key is being transferred (since it never needs to be transferred at all). There is no risk of compromise from the other party’s potential lack of security (since the other party never has your Private key).


its good presentation
Thank you!